Table Of Contents
Category
Security
Artificial Intelligence
AIML
IoT
Blockchain
1. Understanding Credit Card Fraud in the Modern Digital Landscape
Credit card fraud has evolved significantly in the digital age, becoming a pressing concern for consumers and businesses alike. With the rise of online shopping and digital payment methods, fraudsters have found new ways to exploit vulnerabilities in the system. Understanding the landscape of credit card fraud is essential for both consumers and businesses to protect themselves from potential losses.
1.1. The Growing Threat of Payment Fraud: Statistics and Trends
The statistics surrounding credit card fraud are alarming. According to recent studies, payment fraud losses are projected to reach $40 billion by 2027, highlighting the urgency of addressing this issue.
- In 2022, 47% of consumers reported experiencing some form of payment fraud, a significant increase from previous years.
- The rise of e-commerce has contributed to a 30% increase in online payment fraud incidents.
- Card-not-present (CNP) fraud accounts for over 70% of all credit card fraud cases, as online transactions become more prevalent.
These trends indicate that as digital transactions grow, so does the sophistication of fraud schemes. Businesses must stay vigilant and adopt robust security measures to combat these threats, including credit card fraud detection and credit card fraud prevention strategies.
1.2. What Are the Most Common Credit Card Fraud Schemes?
Credit card fraud schemes can take various forms, each with its own tactics and methods. Understanding these schemes is crucial for identifying and preventing fraud.
- Phishing Scams: Fraudsters often use emails or fake websites to trick individuals into providing their credit card information. These scams can be highly convincing, making it essential for consumers to verify the authenticity of requests for sensitive information.
- Card Skimming: This technique involves the use of devices that capture card information from unsuspecting victims at ATMs or point-of-sale terminals. Skimmers can be difficult to detect, so consumers should always inspect machines for any unusual attachments. To avoid credit card skimming, consumers should be vigilant and report any suspicious devices.
- Account Takeover: In this scheme, fraudsters gain access to a victim's account by stealing login credentials. Once they have control, they can make unauthorized purchases or change account details. Implementing two-factor authentication can help mitigate this risk.
- Synthetic Identity Fraud: This increasingly common scheme involves creating a new identity using a combination of real and fake information. Fraudsters use these synthetic identities to open credit accounts and make purchases, often leaving victims unaware until significant damage is done.
- Data Breaches: Large-scale data breaches can expose millions of credit card numbers, making it easy for criminals to use stolen information for fraudulent transactions. Businesses must prioritize data security to protect customer information.
To combat these fraud schemes, both consumers and businesses can take proactive steps:
- Monitor Transactions: Regularly check bank statements and transaction history for any unauthorized charges. Advanced technologies such as AI agents are able to detect transaction anomalies and immediately report them to the parties concerned.
- Use Secure Payment Methods: Opt for payment methods that offer additional security features, such as virtual cards or payment apps with encryption. The best credit card for fraud prevention often includes features like real-time alerts and zero liability for unauthorized transactions.
- Educate Yourself: Stay informed about the latest fraud trends and tactics to recognize potential threats, including ways to prevent credit card fraud and credit card theft.
- Report Suspicious Activity: Immediately report any suspicious transactions to your bank or credit card issuer to minimize potential losses.
At Rapid Innovation, we leverage advanced AI technologies to help businesses enhance their fraud detection capabilities. By implementing machine learning algorithms, we can analyze transaction patterns in real-time, identifying anomalies that may indicate fraudulent activity. This proactive approach not only helps in minimizing losses but also enhances customer trust, ultimately leading to greater ROI for our clients.
By understanding the landscape of credit card fraud and implementing effective security measures, such as credit card fraud prevention for businesses and merchants, consumers and businesses can better protect themselves in the modern digital environment. Additionally, exploring ecommerce credit card fraud prevention strategies can further safeguard online transactions.
1.3. How Does Credit Card Fraud Impact Business Revenue?
Credit card fraud can have a significant negative impact on business revenue. The financial repercussions extend beyond immediate losses, affecting various aspects of a business's operations and reputation.
- Direct Financial Losses: Businesses often bear the cost of fraudulent transactions. According to a report, the global cost of credit card fraud is expected to reach $40.62 billion by 2027. This includes chargebacks, which occur when a customer disputes a transaction, leading to a loss for the merchant.
- Increased Operational Costs: To combat credit card fraud, businesses may need to invest in advanced security measures, such as fraud detection systems and employee training. These investments can strain budgets, especially for small to medium-sized enterprises.
- Reputation Damage: A business that experiences frequent credit card fraud incidents may suffer from a tarnished reputation. Customers may lose trust, leading to decreased sales and customer loyalty. A study found that 60% of consumers would stop doing business with a company after a data breach.
- Legal and Compliance Costs: Businesses may face legal repercussions if they fail to protect customer data adequately. Compliance with regulations like PCI DSS (Payment Card Industry Data Security Standard) can incur additional costs.
- Customer Retention Issues: Credit card fraud can lead to customer dissatisfaction. If customers feel unsafe using their credit cards, they may choose to shop elsewhere, resulting in lost revenue.
2. Which Machine Learning Methods Work Best for Fraud Detection?
Machine learning (ML) has become a vital tool in detecting and preventing credit card fraud. Various methods can be employed, each with its strengths and weaknesses.
- Decision Trees: This method uses a tree-like model of decisions and their possible consequences. It is easy to interpret and can handle both numerical and categorical data effectively.
- Random Forests: An ensemble method that combines multiple decision trees to improve accuracy. It reduces the risk of overfitting and is particularly effective in handling large datasets.
- Support Vector Machines (SVM): SVMs are effective in high-dimensional spaces and can be used for both classification and regression tasks. They work well for credit card fraud detection by finding the optimal hyperplane that separates fraudulent and legitimate transactions.
- Neural Networks: Deep learning models can capture complex patterns in data. They are particularly useful for large datasets and can improve detection rates by learning from vast amounts of transaction data.
- Anomaly Detection: This method identifies unusual patterns that deviate from the norm. Techniques like Isolation Forest and One-Class SVM are commonly used for this purpose.
2.1. Supervised vs. Unsupervised Learning in Fraud Analytics

In fraud analytics, the choice between supervised and unsupervised learning methods can significantly impact the effectiveness of fraud detection systems.
- Supervised Learning: This involves training a model on labeled data, where the outcome (fraudulent or legitimate) is known. Common algorithms include logistic regression, decision trees, and neural networks.
- Pros: High accuracy when sufficient labeled data is available; effective for known fraud patterns.
- Cons: Requires extensive labeled datasets, which can be challenging to obtain.
- Unsupervised Learning: This involves training a model on unlabeled data, allowing the algorithm to identify patterns and anomalies without prior knowledge of outcomes. Techniques include clustering algorithms like K-means and hierarchical clustering.
- Pros: Useful for discovering new credit card fraud patterns; does not require labeled data.
- Cons: May produce false positives; less accurate than supervised methods in some cases.
In conclusion, both supervised and unsupervised learning methods have their place in fraud detection. The choice depends on the specific needs of the business, the availability of data, and the complexity of the fraud patterns being analyzed. At Rapid Innovation, we leverage these machine learning techniques to develop tailored fraud detection solutions that enhance security, reduce losses, and ultimately drive greater ROI for our clients. By implementing advanced AI-driven systems, we help businesses not only mitigate risks but also foster customer trust and loyalty, ensuring sustainable growth in a competitive landscape.
2.2. What Are the Best ML Algorithms for Transaction Monitoring?
Machine learning (ML) algorithms play a crucial role in transaction monitoring, especially in detecting fraudulent activities. The best algorithms for this purpose include:
- Decision Trees: These algorithms are easy to interpret and visualize. They work by splitting the data into branches based on feature values, making them effective for identifying patterns in transaction data.
- Random Forest: An ensemble method that combines multiple decision trees to improve accuracy and reduce overfitting. It is particularly useful in handling large datasets with numerous features.
- Support Vector Machines (SVM): SVMs are effective in high-dimensional spaces and are used for classification tasks. They can help distinguish between legitimate and fraudulent transactions by finding the optimal hyperplane that separates the two classes.
- Neural Networks: Deep learning models can capture complex patterns in transaction data. They are particularly useful for large datasets and can adapt to new types of fraud as they learn from more data.
- Anomaly Detection Algorithms: Techniques like Isolation Forest and One-Class SVM are specifically designed to identify outliers in data, making them suitable for detecting unusual transaction patterns that may indicate fraud.
- Gradient Boosting Machines (GBM): These algorithms build models in a stage-wise fashion and are known for their predictive accuracy. They can handle various types of data and are effective in identifying subtle patterns in transaction data.
At Rapid Innovation, we leverage these advanced transaction monitoring algorithms to help our clients enhance their transaction monitoring systems. By implementing tailored solutions that utilize these algorithms, we enable organizations to detect fraudulent activities more efficiently, ultimately leading to a greater return on investment (ROI).
2.3. Real-time vs. Batch Processing Approaches
When it comes to transaction monitoring, organizations can choose between real-time and batch processing approaches. Each has its advantages and disadvantages:
- Real-time Processing:
- Immediate Detection: Transactions are analyzed as they occur, allowing for instant fraud detection and prevention.
- User Experience: Enhances customer experience by minimizing false declines and ensuring legitimate transactions are processed quickly.
- Resource Intensive: Requires significant computational resources and infrastructure to handle high volumes of transactions in real-time.
- Batch Processing:
- Cost-Effective: Processes transactions in groups at scheduled intervals, which can be more efficient in terms of resource usage.
- Comprehensive Analysis: Allows for more extensive data analysis, as the system can consider a larger dataset at once.
- Delayed Response: Fraud detection may not be immediate, which can lead to potential losses if fraudulent transactions are not caught quickly.
Organizations often choose a hybrid approach, leveraging the strengths of both methods to optimize fraud detection while maintaining operational efficiency. Rapid Innovation assists clients in determining the best approach for their specific needs, ensuring that they achieve optimal results in fraud detection and resource management.
3. How to Build a Robust Credit Card Fraud Detection System?

Building a robust credit card fraud detection system involves several key steps:
- Data Collection: Gather historical transaction data, including both legitimate and fraudulent transactions. Ensure data includes relevant features such as transaction amount, location, time, and user behavior.
- Data Preprocessing: Clean the data to remove duplicates and irrelevant information. Normalize and standardize features to ensure consistency across the dataset.
- Feature Engineering: Create new features that may help in identifying fraud, such as transaction frequency, average transaction amount, and user spending patterns. Use domain knowledge to identify critical features that may indicate fraudulent behavior.
- Model Selection: Choose appropriate ML algorithms based on the data characteristics and business requirements. Consider using ensemble methods to improve accuracy and robustness.
- Model Training and Validation: Split the dataset into training and testing sets to evaluate model performance. Use techniques like cross-validation to ensure the model generalizes well to unseen data.
- Deployment: Integrate the model into the transaction processing system for real-time monitoring. Set up alerts for suspicious transactions and establish a review process for flagged transactions.
- Continuous Improvement: Regularly update the model with new data to adapt to evolving fraud patterns. Monitor system performance and make adjustments as necessary to improve detection rates.
By following these steps, organizations can create a robust credit card fraud detection system that effectively minimizes losses and enhances security. At Rapid Innovation, we provide comprehensive consulting and development services to guide clients through this process, ensuring they build effective systems that align with their business goals.
3.1. Data Collection and Feature Engineering Strategies
Data collection is the foundation of any machine learning (ML) project, especially in fraud detection. The quality and quantity of data directly influence the model's performance. Here are some effective strategies for data collection and feature engineering that Rapid Innovation employs to help clients achieve greater ROI:
- Identify Data Sources: Gather data from various sources such as transaction logs, user profiles, and external databases. This can include:
- Transaction history
- User behavior data
- Device information
- Geolocation data
- Data Cleaning: Ensure the data is clean and free from errors. This involves:
- Removing duplicates
- Handling missing values
- Correcting inconsistencies
- Feature Selection: Choose relevant features that can help in identifying fraudulent activities. Common features include:
- Transaction amount
- Time of transaction
- Frequency of transactions
- User location
- Feature Engineering: Create new features that can enhance the model's predictive power. Techniques include:
- Aggregating transaction data over time (e.g., total spent in the last week)
- Creating binary features (e.g., whether the transaction is above a certain threshold)
- Encoding categorical variables (e.g., using one-hot encoding for user types)
- Data Transformation: Normalize or standardize data to ensure that all features contribute equally to the model. This can involve:
- Scaling numerical features
- Log transformation for skewed distributions
3.2. How to Select the Right ML Model for Fraud Detection?
Selecting or developing the right machine learning model is crucial for effective fraud detection. The choice of model can significantly impact the accuracy and efficiency of detecting fraudulent transactions. Here are some steps to guide the selection process, which Rapid Innovation utilizes to optimize client outcomes:
- Understand the Problem: Determine whether the problem is a classification (fraud vs. non-fraud) or regression (predicting the likelihood of fraud) task.
- Evaluate Model Types: Consider various ML models suitable for fraud detection, such as:
- Decision Trees
- Random Forests
- Gradient Boosting Machines (GBM)
- Neural Networks
- Support Vector Machines (SVM)
- Consider Interpretability: In fraud detection, model interpretability is essential for understanding why a transaction is flagged. Models like Decision Trees and Logistic Regression are more interpretable compared to complex models like Neural Networks.
- Assess Performance Metrics: Use appropriate metrics to evaluate model performance, such as:
- Precision
- Recall
- F1 Score
- Area Under the Receiver Operating Characteristic Curve (AUC-ROC)
- Cross-Validation: Implement cross-validation techniques to ensure the model's robustness and avoid overfitting. This involves:
- Splitting the dataset into training and testing sets
- Using k-fold cross-validation to assess model performance
3.3. Handling Imbalanced Transaction Datasets
Imbalanced datasets are common in fraud detection, where fraudulent transactions are significantly fewer than legitimate ones. Addressing this imbalance is crucial for building an effective model. Here are strategies to handle imbalanced datasets that Rapid Innovation applies to enhance client fraud detection capabilities:
- Resampling Techniques: Adjust the dataset to balance the classes. This can be done through:
- Oversampling: Increase the number of fraudulent transactions by duplicating them or generating synthetic samples using techniques like SMOTE (Synthetic Minority Over-sampling Technique).
- Undersampling: Reduce the number of legitimate transactions to match the number of fraudulent ones, though this may lead to loss of valuable data.
- Use of Anomaly Detection Models: Consider using models specifically designed for anomaly detection, which can effectively identify rare events in imbalanced datasets.
- Cost-sensitive Learning: Implement algorithms that take the cost of misclassification into account. This can involve:
- Assigning higher penalties for misclassifying fraudulent transactions compared to legitimate ones.
- Ensemble Methods: Utilize ensemble techniques like bagging and boosting to improve model performance on imbalanced datasets. These methods can help in focusing on the minority class during training.
By employing these fraud detection strategies, Rapid Innovation empowers organizations to enhance their fraud detection capabilities, ensuring a more secure transaction environment and ultimately achieving greater business efficiency and effectiveness.
4. What Advanced ML Techniques Prevent Credit Card Fraud?
Credit card fraud is a significant concern for financial institutions and consumers alike. Advanced machine learning (ML) techniques are increasingly being employed to combat this issue. These techniques leverage vast amounts of transaction data to identify patterns and anomalies that may indicate fraudulent activity, such as credit card fraud detection and credit card skimmer detection.
- Machine learning algorithms can analyze historical transaction data to create models that predict the likelihood of fraud, including credit card fraud detection data.
- Techniques such as supervised learning, unsupervised learning, and reinforcement learning are commonly used in fraud detection systems, including credit card fraud detection software.
- The integration of real-time data processing allows for immediate action when suspicious activity is detected, which is crucial for online transaction fraud detection.
4.1. How Can Deep Learning Improve Fraud Detection?
Deep learning, a subset of machine learning, utilizes neural networks with multiple layers to analyze complex data patterns. This approach significantly enhances fraud detection capabilities, particularly in credit card fraud detection systems.
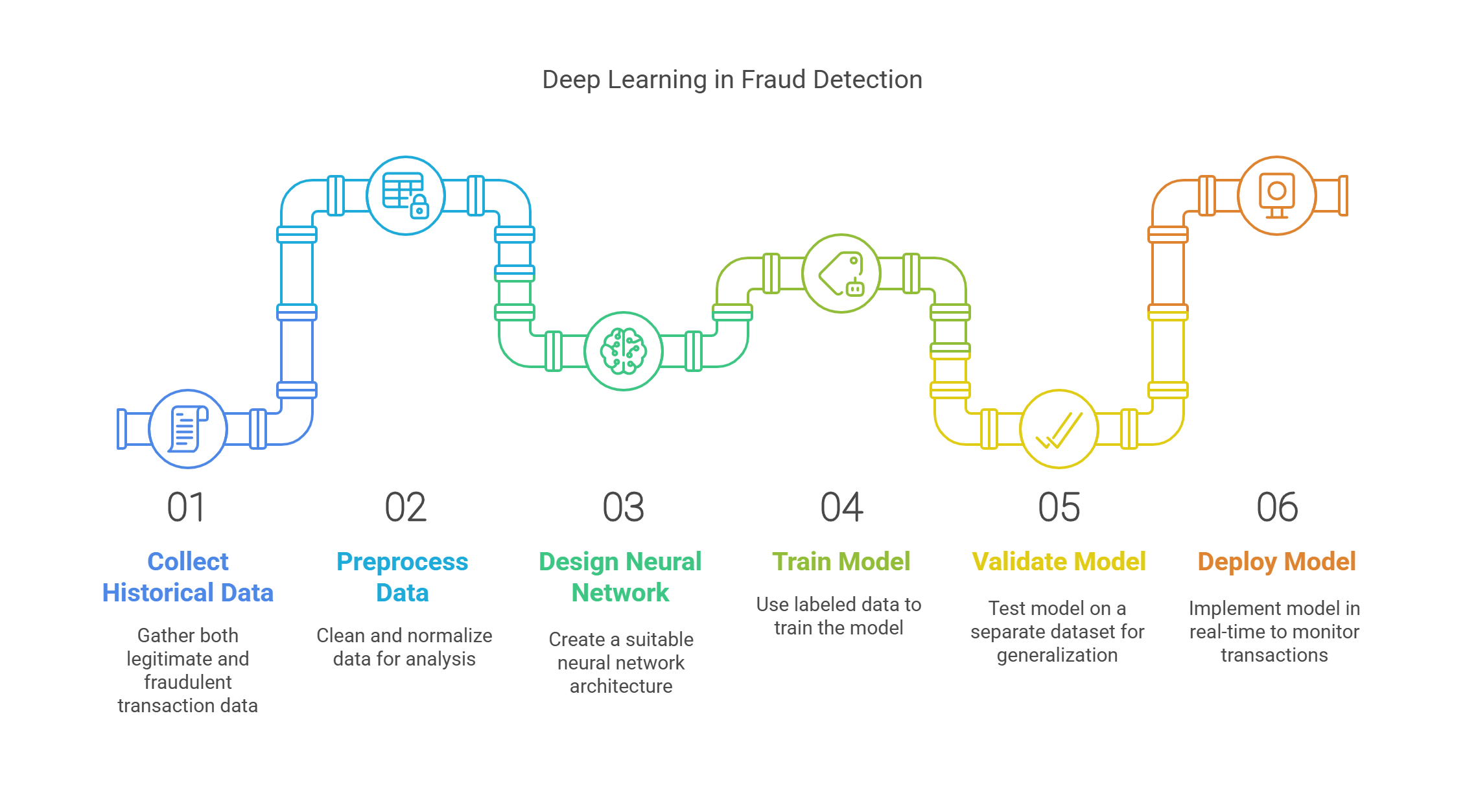
- Feature Extraction: Deep learning models automatically extract relevant features from raw transaction data, reducing the need for manual feature engineering, which is essential for credit card fraud detection kaggle projects.
- Pattern Recognition: These models can identify intricate patterns in transaction behavior that traditional algorithms might miss, improving the effectiveness of credit card fraud monitoring.
- Scalability: Deep learning systems can handle large datasets efficiently, making them suitable for financial institutions with millions of transactions daily, as seen in kaggle credit card fraud detection competitions.
To implement deep learning for fraud detection, follow these steps:
- Collect historical transaction data, including both legitimate and fraudulent transactions, to build a robust credit card fraud detection system.
- Preprocess the data to normalize and clean it for analysis.
- Design a neural network architecture suitable for the task (e.g., convolutional neural networks for image data or recurrent neural networks for sequential data).
- Train the model using labeled data, adjusting hyperparameters to optimize performance.
- Validate the model on a separate dataset to ensure it generalizes well to unseen data.
- Deploy the model in a real-time environment to monitor transactions and flag suspicious activities, similar to how credit card fraud detection apps operate.
4.2. Anomaly Detection Using Behavioral Analytics
Anomaly detection is a critical component of fraud prevention, focusing on identifying unusual patterns in user behavior. Behavioral analytics can enhance this process by providing insights into how users typically interact with their accounts, which is vital for credit card fraud detection.
- User Profiling: Establish baseline behavior for each user, including transaction frequency, amount, and location, which can help in credit card fraud detection.
- Real-Time Monitoring: Continuously analyze transactions against established user profiles to detect deviations, similar to the functionality of a gas pump skimmer detector.
- Contextual Analysis: Consider external factors such as time of day, device used, and geographical location to assess the legitimacy of transactions.
To implement anomaly detection using behavioral analytics, consider the following steps:
- Gather data on user behavior, including transaction history, login patterns, and device information.
- Create user profiles that capture normal behavior patterns.
- Develop algorithms to monitor transactions in real-time, comparing them against established profiles.
- Set thresholds for what constitutes an anomaly, adjusting them based on the risk appetite of the organization.
- Implement alert systems to notify fraud analysts of potential fraudulent transactions for further investigation, enhancing the capabilities of credit card fraud detection systems.
By leveraging advanced ML techniques such as deep learning and anomaly detection through behavioral analytics, financial institutions can significantly enhance their ability to prevent credit card fraud. These methods not only improve detection rates but also reduce false positives, ensuring a better experience for legitimate customers.
At Rapid Innovation, we specialize in implementing these advanced ML techniques for fintech tailored to your organization's specific needs. Our expertise in AI development and consulting ensures that you can achieve greater ROI by effectively mitigating fraud risks while enhancing customer satisfaction. Let us help you navigate the complexities of fraud detection and prevention, empowering your business to thrive in a secure environment.
4.3. Ensemble Methods for Enhanced Accuracy
Ensemble methods are powerful techniques in machine learning that combine multiple models to improve predictive performance. By leveraging the strengths of various algorithms, ensemble methods can significantly enhance accuracy and robustness, ultimately helping businesses achieve their goals more efficiently.
Types of Ensemble Methods
- Bagging: This method involves training multiple models independently on different subsets of the data and then averaging their predictions. Random Forest is a popular example of bagging, which reduces variance and helps prevent overfitting. Rapid Innovation utilizes bagging techniques, such as bagging machine learning and bagging ensemble methods, to enhance model stability, ensuring clients receive reliable predictions.
- Boosting: Boosting focuses on sequentially training models, where each new model attempts to correct the errors made by the previous ones. Algorithms like AdaBoost and Gradient Boosting are widely used for their ability to improve accuracy by focusing on difficult-to-predict instances. By implementing boosting strategies, including boosting ensemble and ensemble boosting, Rapid Innovation helps clients achieve higher accuracy in their predictive analytics.
- Stacking: In stacking, multiple models are trained, and their predictions are combined using another model, often referred to as a meta-learner. This method can capture complex relationships in the data and improve overall performance. Rapid Innovation employs stacking to create robust solutions tailored to specific business needs, utilizing ensemble techniques in machine learning.
Benefits of Ensemble Methods
- Improved Accuracy: Ensemble methods often outperform individual models by reducing bias and variance, leading to better decision-making for clients. Techniques such as ensemble learning methods and ensemble learning algorithms contribute to this improvement.
- Robustness: They are less sensitive to noise and outliers, making them suitable for real-world applications. Rapid Innovation ensures that clients' models are resilient and can handle diverse data scenarios, leveraging ensemble techniques machine learning.
- Flexibility: Ensemble methods can be applied to various types of models, including decision trees, neural networks, and support vector machines, allowing Rapid Innovation to customize solutions for different industries. This includes ensemble neural networks and ensemble machine learning models.
Implementation Steps
- Select base models to include in the ensemble.
- Choose an ensemble technique (bagging, boosting, or stacking).
- Train the base models on the training dataset.
- Combine the predictions from the base models using the chosen method.
- Evaluate the ensemble model's performance on a validation dataset.
5. Implementation Challenges and Solutions
Implementing machine learning models, especially ensemble methods, comes with its own set of challenges. Addressing these challenges is crucial for achieving optimal performance and maximizing ROI for clients.
Common Challenges
- Data Quality: Poor quality data can lead to inaccurate predictions. Ensuring data is clean, complete, and relevant is essential for effective model performance.
- Model Complexity: Ensemble methods can become complex, making them harder to interpret and manage. This complexity can lead to longer training times and increased resource consumption.
- Overfitting: While ensemble methods can reduce overfitting, they can still be prone to it if not properly tuned.
Solutions to Challenges
- Data Preprocessing: Implement robust data cleaning and preprocessing techniques to enhance data quality. This includes handling missing values, outlier detection, and normalization, which Rapid Innovation prioritizes to ensure high-quality inputs for models.
- Model Selection: Choose a balanced number of models for the ensemble to avoid excessive complexity. Use techniques like cross-validation to assess model performance, ensuring that clients receive the best possible outcomes.
- Regularization Techniques: Apply regularization methods to prevent overfitting, such as L1 or L2 regularization, especially in boosting algorithms. Rapid Innovation employs these techniques to fine-tune models for optimal performance.
5.1. Balancing Security with Customer Experience
In the realm of machine learning, particularly in applications involving sensitive data, balancing security with customer experience is paramount. Organizations must ensure that their models are not only accurate but also secure against potential threats.
Key Considerations
- Data Privacy: Implement strong data protection measures to safeguard customer information. This includes encryption and anonymization techniques, which Rapid Innovation integrates into its solutions.
- User Experience: Ensure that security measures do not hinder the user experience. For instance, overly complex authentication processes can frustrate users, impacting overall satisfaction.
- Compliance: Adhere to regulations such as GDPR or CCPA to maintain customer trust and avoid legal repercussions.
Strategies for Balance
- Adaptive Security Measures: Use adaptive security protocols that adjust based on user behavior, providing a seamless experience while maintaining security.
- User Education: Educate customers about security practices, helping them understand the importance of security without compromising their experience.
- Feedback Mechanisms: Implement feedback loops to gather user input on security measures, allowing for continuous improvement in both security and user experience.
By addressing these points, organizations can effectively leverage ensemble methods while navigating the complexities of implementation and maintaining a balance between security and customer experience. Rapid Innovation is committed to guiding clients through these challenges, ensuring they achieve their business goals efficiently and effectively. For more insights on overcoming challenges in machine learning, you can read about debugging and troubleshooting common issues in computer vision models.
5.2. Managing False Positives and Alert Fatigue
False positives in fraud detection can lead to significant operational inefficiencies and alert fatigue among security teams. When legitimate transactions are flagged as fraudulent, it not only wastes resources but can also frustrate customers. To effectively manage false positives and alert fatigue, organizations can implement the following strategies:
- Refine Detection Algorithms: Utilize machine learning models that adapt over time. These models can learn from historical data to improve accuracy in identifying genuine fraud cases, thereby enhancing the overall efficiency of fraud detection systems.
- Implement Risk Scoring: Assign risk scores to transactions based on various parameters such as transaction amount, location, and user behavior. This helps prioritize alerts, allowing teams to focus on high-risk transactions first, which can lead to a more effective allocation of resources.
- Continuous Monitoring and Feedback Loops: Establish a feedback mechanism where analysts can provide input on false positives. This data can be used to retrain models and improve detection accuracy, ensuring that the system evolves with changing fraud patterns.
- User Behavior Analytics (UBA): Leverage UBA to create a baseline of normal user behavior. Any significant deviation from this baseline can trigger alerts, reducing the chances of false positives and improving the user experience.
- Automated Triage Systems: Implement automated systems that can categorize alerts based on severity. This helps in filtering out low-risk alerts, allowing analysts to concentrate on more critical issues, thus enhancing operational efficiency.
Organizations can also adopt fraud detection strategies that focus on minimizing false positives while ensuring robust security measures are in place.
5.3. Scaling Fraud Detection Infrastructure
As businesses grow, so does the volume of transactions and the complexity of fraud schemes. Scaling fraud detection infrastructure is crucial to maintaining effective security measures. Here are some strategies to consider:
- Cloud-Based Solutions: Utilize cloud services to enhance scalability. Cloud platforms can handle large volumes of data and provide the flexibility to scale resources up or down based on demand, ensuring that fraud detection systems remain robust during peak times.
- Distributed Architecture: Implement a distributed architecture that allows for parallel processing of transactions. This can significantly reduce latency and improve the speed of fraud detection, enabling quicker responses to potential threats.
- Data Integration: Ensure seamless integration of various data sources, including transaction data, user profiles, and external threat intelligence. A holistic view of data can enhance detection capabilities and provide deeper insights into fraud patterns.
- Real-Time Analytics: Invest in real-time analytics tools that can process transactions as they occur. This enables immediate detection of suspicious activities and reduces the window of opportunity for fraudsters, ultimately protecting the bottom line.
- Regular Infrastructure Audits: Conduct regular audits of your fraud detection infrastructure to identify bottlenecks and areas for improvement. This proactive approach can help maintain optimal performance and ensure that the system adapts to evolving threats.
6. Real-world Case Studies and Success Stories
Incorporating real-world case studies can provide valuable insights into effective fraud detection strategies. Here are a few notable examples:
- PayPal: PayPal employs machine learning algorithms to analyze transaction patterns and detect anomalies. By continuously refining their models, they have significantly reduced false positives and improved customer satisfaction, showcasing the effectiveness of advanced AI solutions.
- American Express: American Express uses a combination of user behavior analytics and real-time transaction monitoring. This multi-layered approach has allowed them to detect fraudulent transactions quickly while minimizing disruptions to legitimate users, demonstrating the power of integrated fraud detection systems.
- Netflix: Netflix has implemented a sophisticated fraud detection system that leverages big data analytics. By analyzing user behavior and transaction history, they have successfully reduced subscription fraud and improved overall security, highlighting the importance of data-driven decision-making.
These case studies highlight the importance of adopting advanced technologies and strategies in managing false positives, scaling infrastructure, and ultimately enhancing fraud detection capabilities. At Rapid Innovation, we specialize in developing tailored AI solutions that empower organizations to achieve greater ROI through effective fraud detection and management strategies, including comprehensive fraud prevention and detection strategies.
6.1. How Do Large Enterprises Prevent Credit Card Fraud?
Large enterprises employ a multi-layered approach to prevent credit card fraud, utilizing advanced technologies and strategies to safeguard transactions. Key methods include:
- Fraud Detection Software: Many organizations implement machine learning algorithms that analyze transaction patterns in real-time. These systems can identify anomalies and flag suspicious activities for further investigation. At Rapid Innovation, we specialize in developing customized fraud detection solutions that leverage AI to enhance the accuracy and speed of anomaly detection, ultimately reducing false positives and improving operational efficiency. This includes credit card fraud detection and online credit card fraud detection.
- Tokenization: This process replaces sensitive credit card information with a unique identifier or token. Even if data is intercepted, it cannot be used without the corresponding tokenization system. Our team can assist in integrating tokenization technologies that align with your existing systems, ensuring a seamless transition while enhancing security.
- Two-Factor Authentication (2FA): By requiring an additional verification step, such as a text message or email confirmation, enterprises can significantly reduce the risk of unauthorized access. Rapid Innovation can help implement robust 2FA solutions tailored to your business needs, ensuring that customer data remains secure.
- Regular Security Audits: Conducting frequent audits helps identify vulnerabilities in the system. This proactive approach ensures that security measures are up-to-date and effective. We offer comprehensive security audit services that utilize AI-driven analytics to pinpoint weaknesses and recommend actionable improvements.
- Employee Training: Educating staff about the latest fraud schemes and security protocols is crucial, as employees are often the first line of defense against fraud. Rapid Innovation provides training programs that incorporate AI insights, equipping your team with the knowledge to recognize and respond to potential threats effectively. This includes training on credit card fraud prevention and ways to prevent credit card fraud.
- Collaboration with Financial Institutions: Many enterprises work closely with banks and credit card companies to share information about emerging threats and best practices. We facilitate partnerships and integrations with financial institutions, enhancing your organization's ability to stay ahead of fraud trends, including AI-based fraud prevention for insurance businesses and credit card merchants.
6.2. ROI Analysis and Business Impact Metrics
Understanding the return on investment (ROI) for fraud prevention measures is essential for large enterprises. Effective ROI analysis involves:
- Cost of Fraud: Calculate the total losses incurred due to fraud, including chargebacks, fines, and reputational damage. According to a report, businesses lose an average of 5% of their revenue to fraud annually.
- Investment in Technology: Assess the costs associated with implementing fraud prevention technologies, such as software, hardware, and training. Rapid Innovation can help you evaluate the most cost-effective solutions that maximize your investment in technology.
- Operational Efficiency: Evaluate how fraud prevention measures improve operational efficiency. For instance, automated systems can reduce the time spent on manual reviews. Our AI solutions streamline processes, allowing your team to focus on strategic initiatives rather than routine tasks.
- Customer Trust and Retention: Measure the impact of fraud prevention on customer satisfaction and loyalty. A secure shopping experience can lead to increased sales and repeat customers. By enhancing security measures, we help you build stronger relationships with your customers, which is crucial for credit card fraud management.
- Compliance Costs: Consider the expenses related to adhering to regulations, such as PCI DSS (Payment Card Industry Data Security Standard). Non-compliance can result in hefty fines. Rapid Innovation ensures that your systems are compliant with the latest regulations, minimizing the risk of financial penalties.
6.3. Lessons Learned from Major Fraud Prevention Programs

While not always necessary, analyzing lessons learned from major fraud prevention programs can provide valuable insights. Key takeaways include:
- Adaptability: Fraud tactics evolve rapidly. Successful programs are those that can adapt to new threats and continuously update their strategies. Our AI-driven solutions are designed to learn and adapt, ensuring your defenses remain robust against emerging threats, including card fraud prevention.
- Data-Driven Decisions: Utilizing data analytics to inform decisions can lead to more effective fraud prevention measures. Organizations that rely on data are better equipped to identify trends and adjust their approaches accordingly. Rapid Innovation specializes in data analytics, providing insights that drive informed decision-making.
- Cross-Department Collaboration: Fraud prevention is not solely the responsibility of the IT department. Successful programs involve collaboration across various departments, including finance, customer service, and compliance. We promote a holistic approach to fraud prevention, ensuring all departments work together seamlessly.
- Customer Education: Informing customers about potential fraud risks and encouraging them to adopt security measures can enhance overall protection. Our solutions include customer-facing tools that educate users on best practices for online security, such as avoiding credit card skimming and credit card skimming prevention.
- Regular Review and Improvement: Continuous assessment of fraud prevention strategies is essential. Organizations should regularly review their policies and technologies to ensure they remain effective against emerging threats. Rapid Innovation offers ongoing support and updates to keep your fraud prevention measures at the forefront of technology.
By implementing these strategies, large enterprises can significantly reduce the risk of credit card fraud, protect their assets, and maintain customer trust. Rapid Innovation is committed to helping you achieve these goals through our tailored AI solutions and expert consulting services, including ecommerce credit card fraud prevention and credit card fraud solutions. Regulatory compliance and risk management are critical components in the financial sector, particularly in the realm of payment processing and fraud detection. Organizations must navigate a complex landscape of global payment security standards and regulations while ensuring data privacy.
7. Regulatory Compliance and Risk Management
7.1. Global Payment Security Standards and Regulations
In the ever-evolving world of digital payments, adhering to global security standards is essential for protecting sensitive financial information. Key regulations include:
- Payment Card Industry Data Security Standard (PCI DSS): This standard is crucial for organizations that handle credit card transactions, including those focused on pci compliance quickbooks and quickbooks pci compliance. It mandates strict security measures to protect cardholder data, including encryption, access control, and regular security testing. Non-compliance can lead to hefty fines and reputational damage.
- General Data Protection Regulation (GDPR): Enforced in the European Union, GDPR sets stringent guidelines for data protection and privacy. Organizations must ensure that personal data is processed lawfully, transparently, and for specific purposes. Non-compliance can result in fines up to 4% of annual global turnover or €20 million, whichever is higher.
- Anti-Money Laundering (AML) Regulations: These regulations require financial institutions to implement measures to detect and prevent money laundering activities. This includes customer due diligence, transaction monitoring, and reporting suspicious activities to authorities.
To comply with these standards, organizations should:
- Conduct regular audits to assess compliance with security standards, including pci compliance saq a.
- Implement robust encryption methods for data protection.
- Train employees on compliance requirements and security best practices, particularly in relation to payment pci compliance and pci compliance policy.
At Rapid Innovation, we leverage AI-driven solutions to help organizations streamline their compliance processes. For instance, our advanced analytics tools can automate the auditing process, ensuring that organizations remain compliant with PCI DSS, GDPR, and AML regulations while significantly reducing operational costs. This not only enhances efficiency but also leads to a greater return on investment (ROI).
7.2. Data Privacy Considerations in Fraud Detection
Data privacy is a significant concern in fraud detection, as organizations must balance the need for effective fraud prevention with the obligation to protect personal information. Key considerations include:
- Data Minimization: Organizations should only collect data that is necessary for fraud detection, which aligns with pci compliance credit card storage. This reduces the risk of exposing sensitive information and aligns with privacy regulations like GDPR.
- Anonymization and Pseudonymization: Techniques such as anonymization and pseudonymization can help protect personal data while still allowing for effective fraud detection. By removing identifiable information, organizations can analyze data without compromising individual privacy.
- User Consent: Obtaining explicit consent from users before collecting or processing their data is essential. Organizations should clearly communicate how data will be used for fraud detection and ensure that users have the option to opt-out.
To implement effective data privacy measures in fraud detection, organizations can follow these steps:
- Develop a clear data privacy policy that outlines data collection, usage, and retention practices.
- Utilize advanced analytics and machine learning algorithms that prioritize data privacy while detecting fraudulent activities, including those related to tokenization and pci compliance.
- Regularly review and update data protection measures to comply with evolving regulations.
At Rapid Innovation, we specialize in deploying machine learning algorithms that not only enhance fraud detection capabilities but also prioritize data privacy. By utilizing our solutions, organizations can achieve a dual benefit: effective fraud prevention and compliance with data privacy regulations, ultimately leading to improved customer trust and loyalty.
In conclusion, regulatory compliance and risk management are vital for organizations involved in payment processing and fraud detection. By adhering to global payment security standards, such as those related to credit card processing pci and merchant pci compliance, and prioritizing data privacy, organizations can effectively mitigate risks while maintaining customer trust. Rapid Innovation is here to support your journey towards achieving these goals efficiently and effectively, ensuring a greater ROI through our tailored AI solutions.
7.3. Building a Compliance-first Security Framework
A compliance-first security framework is essential for organizations to protect sensitive data while adhering to regulatory requirements such as HIPAA and HITRUST certification. This approach ensures that security measures are not only effective but also aligned with legal standards.
- Understand Regulatory Requirements:
- Identify relevant regulations (e.g., GDPR, PCI DSS, HIPAA, NIST).
- Conduct a gap analysis to assess current compliance status, including HITRUST compliance and NIST requirements.
- Develop Policies and Procedures:
- Create comprehensive security policies that reflect compliance requirements, including HITRUST CSF and NIST 800.53.
- Establish procedures for data handling, access control, and incident response.
- Implement Security Controls:
- Utilize encryption for data at rest and in transit.
- Deploy multi-factor authentication (MFA) to enhance access security.
- Regular Training and Awareness:
- Conduct regular training sessions for employees on compliance and security best practices, including HIPAA and HITRUST.
- Foster a culture of security awareness within the organization.
- Continuous Monitoring and Auditing:
- Implement continuous monitoring tools to detect compliance violations.
- Schedule regular audits to assess adherence to security policies and regulations, including NIST auditing and HITRUST CSF certified status.
- Incident Response Plan:
- Develop a robust incident response plan that includes compliance considerations.
- Ensure that the plan is regularly tested and updated based on new threats and regulations.
By prioritizing compliance in your security framework, you can mitigate risks and enhance your organization's reputation. Rapid Innovation can assist in developing and implementing a compliance-first security framework tailored to your specific needs, ensuring that your organization not only meets regulatory requirements but also enhances its overall security posture. Additionally, if you're looking for specialized services, consider our Bitcoin wallet development services to further secure your financial transactions.
8. How to Future-proof Your Fraud Detection Strategy?
As fraud tactics evolve, organizations must adapt their fraud detection strategies to stay ahead. A future-proof strategy incorporates advanced technologies and proactive measures.
- Leverage Machine Learning and AI:
- Implement machine learning algorithms to analyze transaction patterns and detect anomalies.
- Use AI-driven tools for real-time fraud detection and prevention.
- Integrate Behavioral Analytics:
- Monitor user behavior to identify deviations from normal patterns.
- Use behavioral biometrics to enhance identity verification processes.
- Collaborate with Industry Peers:
- Share threat intelligence with other organizations to stay informed about emerging fraud trends.
- Participate in industry forums and workshops to learn from best practices.
- Regularly Update Detection Models:
- Continuously refine fraud detection models based on new data and emerging threats.
- Conduct periodic reviews to ensure models remain effective.
- Invest in Customer Education:
- Educate customers about common fraud schemes and how to protect themselves.
- Provide resources and support for reporting suspicious activities.
By adopting these strategies, organizations can create a resilient fraud detection framework that adapts to changing threats.
8.1. What New Technologies Are Shaping Payment Security?

Emerging technologies are revolutionizing payment security, making transactions safer and more efficient. Understanding these technologies is crucial for organizations looking to enhance their security posture.
- Blockchain Technology:
- Provides a decentralized ledger for secure and transparent transactions.
- Reduces the risk of fraud by ensuring data integrity.
- Tokenization:
- Replaces sensitive payment information with unique tokens.
- Minimizes the risk of data breaches by limiting exposure of card details.
- Biometric Authentication:
- Utilizes fingerprints, facial recognition, or voice recognition for secure access.
- Enhances user experience while improving security.
- Contactless Payments:
- Offers a fast and secure way to make transactions without physical contact.
- Reduces the risk of card skimming and other fraud methods.
- Artificial Intelligence:
- Analyzes vast amounts of transaction data to identify potential fraud.
- Automates decision-making processes for faster response times.
By embracing these technologies, organizations can significantly enhance their payment security and reduce the risk of fraud. Rapid Innovation is positioned to help organizations integrate these advanced technologies into their payment systems, ensuring robust security and compliance while maximizing ROI.
8.2. Adapting to Evolving Fraud Patterns
Fraud patterns are constantly changing, driven by advancements in technology and shifts in consumer behavior. Businesses must remain vigilant and adaptable to these evolving threats to protect their assets and maintain customer trust. Rapid Innovation can assist organizations in this endeavor by leveraging AI-driven solutions tailored to combat fraud effectively.
- Continuous Monitoring: Implement real-time monitoring systems powered by AI to detect unusual activities, including transaction monitoring, user behavior analytics, and anomaly detection algorithms. Our AI solutions can analyze vast amounts of data in real-time, enabling businesses to respond swiftly to potential threats. This includes employing fraud detection strategies to identify and address suspicious activities promptly.
- Data Analysis: Utilize big data analytics to identify trends and patterns in fraud. Machine learning models developed by Rapid Innovation can help predict potential fraud scenarios based on historical data, allowing businesses to proactively address vulnerabilities. This is essential for developing effective fraud prevention strategies.
- Regular Training: Conduct regular training sessions for employees to recognize new fraud tactics. Rapid Innovation can provide customized training programs that incorporate the latest insights on fraud prevention measures, ensuring that staff are well-equipped to identify and mitigate risks.
- Collaboration with Experts: Partner with cybersecurity firms and fraud prevention specialists to stay updated on the latest threats and mitigation strategies. Rapid Innovation can facilitate these partnerships, providing clients with access to a network of experts in the field, enhancing their fraud management strategy.
- Feedback Loops: Establish feedback mechanisms to learn from past fraud incidents. Analyzing what went wrong can help refine strategies and improve future responses. Our AI tools can assist in creating these feedback loops, ensuring that organizations continuously evolve their fraud prevention tactics, including fraud mitigation strategies.
8.3. Investment Planning and Resource Allocation
Effective investment planning and resource allocation are crucial for businesses to thrive in a competitive landscape. Properly allocating resources can enhance operational efficiency and drive growth. Rapid Innovation offers consulting services to help organizations optimize their investment strategies.
- Assessing Needs: Conduct a thorough assessment of current and future business needs, including evaluating technology requirements, workforce capabilities, and market trends. Our team can provide insights into the latest AI technologies that can enhance operational efficiency, including strategies to prevent fraud and corruption.
- Budgeting: Develop a detailed budget that aligns with strategic goals. Allocate funds to high-impact areas such as technology upgrades, employee training, and marketing initiatives. Rapid Innovation can assist in identifying the most effective areas for investment to maximize ROI, including credit card fraud prevention strategy.
- Diversification: Consider diversifying investments to mitigate risks. This can involve investing in different sectors or technologies to ensure stability. Our expertise in emerging technologies can guide clients in making informed diversification decisions, including fraud control strategy.
- Performance Metrics: Establish key performance indicators (KPIs) to measure the effectiveness of resource allocation. Regularly review these metrics to make informed adjustments. Rapid Innovation can help develop AI-driven analytics tools to track and analyze performance metrics effectively, ensuring that fraud prevention strategies in banks are optimized.
- Stakeholder Engagement: Involve key stakeholders in the investment planning process, as their insights can provide valuable perspectives on resource allocation priorities. Our consulting services can facilitate stakeholder engagement sessions to ensure alignment on strategic goals, including strategies to combat fraud and corruption.
9. Best Practices for Business Leaders
Business leaders play a pivotal role in steering their organizations toward success. Adopting best practices can enhance decision-making and foster a culture of accountability. Rapid Innovation encourages leaders to embrace these practices to drive innovation and growth.
- Transparent Communication: Foster open lines of communication within the organization. Transparency builds trust and encourages collaboration among teams.
- Data-Driven Decisions: Leverage data analytics to inform strategic decisions. Relying on data can reduce biases and lead to more effective outcomes. Rapid Innovation's AI solutions can provide actionable insights to support data-driven decision-making, including fraud risk strategy.
- Agility and Flexibility: Cultivate an agile organizational culture that can quickly adapt to changes, including being open to new ideas and adjusting strategies as needed.
- Employee Empowerment: Empower employees by providing them with the tools and resources they need to succeed. Encouraging autonomy can lead to increased innovation and productivity, particularly in implementing fraud prevention tactics.
- Regular Reviews: Conduct regular performance reviews to assess progress toward goals. This allows for timely adjustments and reinforces accountability.
By focusing on adapting to evolving fraud patterns, effective investment planning, and implementing best practices, businesses can enhance their resilience and drive sustainable growth with the support of Rapid Innovation's AI-driven solutions.
9.1. How to Create an Effective Fraud Prevention Strategy?
Creating an effective fraud prevention strategy is essential for organizations to safeguard their assets and maintain customer trust. A comprehensive approach involves several key components:
- Risk Assessment: Identify potential fraud risks specific to your industry and organization. This includes understanding the types of fraud prevalent in your sector, such as identity theft, payment fraud, or account takeover. Implementing fraud risk strategy is crucial in this phase.
- Data Analytics: Utilize advanced data analytics tools to monitor transactions in real-time. Machine learning algorithms can help detect anomalies and flag suspicious activities, enabling organizations to respond swiftly and effectively. This is a key aspect of fraud detection strategies.
- Employee Training: Regularly train employees on fraud awareness and prevention techniques. This ensures that all staff members are vigilant and can recognize potential fraud indicators, fostering a culture of security within the organization. Training should include fraud prevention tactics and measures.
- Multi-Factor Authentication (MFA): Implement MFA for sensitive transactions. This adds an extra layer of security, making it harder for fraudsters to gain unauthorized access and enhancing overall transaction integrity. This is part of a broader fraud management strategy.
- Incident Response Plan: Develop a clear incident response plan that outlines steps to take in the event of a fraud occurrence. This should include communication protocols and recovery strategies, ensuring a coordinated response to incidents. This is essential for effective fraud mitigation strategies.
- Regular Audits: Conduct regular audits of your fraud prevention measures to identify weaknesses and areas for improvement. This can help in adapting to new fraud tactics and ensuring that your strategy remains effective. Regular audits are a critical component of fraud prevention strategies using AI in banks.
9.2. How to Build and Train a Fraud Analysis Team?

Building a competent fraud analysis team is crucial for effective fraud detection and prevention. Here are steps to create and train such a team:
- Define Roles and Responsibilities: Clearly outline the roles within the team, such as fraud analysts, investigators, and data scientists. Each member should have specific responsibilities to ensure comprehensive coverage.
- Recruitment: Hire individuals with a background in finance, data analysis, or law enforcement. Look for candidates with analytical skills and experience in fraud detection, as these attributes are essential for effective analysis.
- Training Programs: Develop training programs that cover fraud detection techniques, data analysis tools and software, legal and regulatory compliance, and case studies of past fraud incidents. This equips the team with the necessary skills to combat fraud effectively, including strategies to prevent fraud and corruption.
- Continuous Learning: Encourage team members to participate in workshops, webinars, and industry conferences. This keeps them updated on the latest fraud trends and technologies, ensuring that your team remains at the forefront of fraud prevention.
- Collaboration: Foster a collaborative environment where team members can share insights and strategies. Regular team meetings can help in discussing ongoing cases and refining detection methods, enhancing overall team performance.
- Performance Metrics: Establish performance metrics to evaluate the effectiveness of the team. This can include the number of fraud cases detected, response times, and successful recoveries, providing a clear picture of the team's impact.
9.3. Measuring and Optimizing Detection Performance
Measuring and optimizing detection performance is vital for ensuring the effectiveness of your fraud prevention strategy. Here are key steps to achieve this:
- Set Key Performance Indicators (KPIs): Define KPIs that align with your fraud prevention goals. Common KPIs include the detection rate of fraudulent transactions, false positive rate, and time taken to resolve fraud cases.
- Data Analysis: Regularly analyze data to assess the performance of your fraud detection systems. Look for patterns in false positives and adjust algorithms accordingly, ensuring that your systems remain accurate and efficient.
- Feedback Loop: Create a feedback loop where insights from fraud cases are used to refine detection methods. This helps in adapting to evolving fraud tactics and improving overall detection capabilities.
- Benchmarking: Compare your performance metrics against industry standards. This can provide insights into areas where your organization may need improvement, allowing for targeted enhancements.
- Technology Upgrades: Stay updated with the latest fraud detection technologies. Implementing advanced tools can enhance detection capabilities and reduce false positives, ultimately leading to greater efficiency.
- Regular Reviews: Conduct regular reviews of your fraud detection performance. This should include assessing the effectiveness of training programs and team performance, ensuring continuous improvement.
By following these guidelines, organizations can create a robust fraud prevention strategy, build a skilled fraud analysis team, and continuously optimize their detection performance. Rapid Innovation is here to assist you in implementing these strategies effectively, leveraging our expertise in AI and data analytics to help you achieve greater ROI and safeguard your business against fraud. Implementing fraud detection implementation in your business is crucial for safeguarding your assets and maintaining customer trust. With the rise of digital transactions, the need for robust fraud detection systems has never been more pressing.
10. How to Implement Fraud Detection in Your Business?
10.1. What Are the Steps to Deploy Fraud Detection?
Deploying a fraud detection system involves several key steps, and Rapid Innovation is here to guide you through each one:
- Identify Fraud Risks: Our team will work with you to assess your business model, identifying potential fraud risks and analyzing historical data to understand common fraud patterns specific to your industry.
- Choose the Right Technology: We help you select a fraud detection solution that fits your business needs. Options include advanced machine learning algorithms, rule-based systems, or third-party services. We prioritize solutions that offer real-time monitoring and alerts to enhance your operational efficiency.
- Data Collection and Integration: Rapid Innovation assists in gathering relevant data from various sources, including transaction records, customer behavior, and external databases. We ensure that your data is clean and structured for effective analysis.
- Develop Fraud Detection Models: Our experts utilize statistical methods or machine learning to create models that can accurately identify fraudulent activities. We train these models using historical data to improve their accuracy and effectiveness.
- Test and Validate: We conduct rigorous testing of your fraud detection system to ensure it accurately identifies fraud without generating excessive false positives. Our validation process includes real-world scenarios to assess the system's effectiveness.
- Implement and Monitor: Rapid Innovation will deploy the fraud detection system across your business operations, continuously monitoring its performance and making necessary adjustments to optimize results.
- Educate Employees: We provide training for your staff on recognizing signs of fraud and how to respond to alerts from the detection system. Our goal is to foster a culture of vigilance and accountability within your organization.
10.2. How to Integrate with Existing Payment Systems?
Integrating fraud detection implementation with your existing payment systems is essential for seamless operations. Here’s how Rapid Innovation can facilitate this integration:
- Assess Compatibility: We evaluate your current payment systems to determine compatibility with the fraud detection solution, checking for APIs or integration capabilities that facilitate communication between systems.
- Choose Integration Method: Our team will help you decide whether to use a direct API integration or a middleware solution that connects your payment system with the fraud detection tool. We also consider using webhooks for real-time data transfer.
- Implement Security Protocols: Rapid Innovation ensures that data exchanged between systems is encrypted to protect sensitive information. We follow industry standards for data security, such as PCI DSS compliance.
- Test the Integration: We conduct thorough testing to ensure that the fraud detection system accurately analyzes transactions from your payment systems. Our simulations of various transaction scenarios validate the integration's effectiveness.
- Monitor Performance: After integration, we continuously monitor the system for any discrepancies or issues, using analytics to assess the effectiveness of the fraud detection in real-time transactions.
- Iterate and Improve: Rapid Innovation regularly updates your fraud detection algorithms based on new fraud patterns and trends. We gather feedback from users to enhance the integration process continually.

By following these steps, businesses can effectively implement fraud detection systems that not only protect against fraudulent activities but also enhance overall operational efficiency. The integration with existing payment systems ensures that fraud detection is a seamless part of the transaction process, providing a robust defense against potential threats. With Rapid Innovation's expertise, you can achieve your business goals efficiently and effectively, maximizing your return on investment.
10.3. Training and Maintenance Protocols
Training and maintenance protocols are essential components in ensuring the effective operation and longevity of systems, whether they are software applications, machinery, or any other technology. These training and maintenance protocols help in optimizing performance, minimizing downtime, and ensuring that users are well-equipped to handle the systems they work with.
Importance of Training Protocols
- Training protocols are designed to equip users with the necessary skills and knowledge to operate systems effectively.
- They help in reducing errors and increasing productivity by ensuring that users understand the functionalities and features of the system.
- Regular training sessions can keep users updated on new features, best practices, and troubleshooting techniques.
Components of Effective Training Protocols
- Needs Assessment: Identify the specific skills and knowledge gaps among users.
- Curriculum Development: Create a structured training program that covers all essential aspects of the system.
- Training Methods: Utilize a mix of training methods such as hands-on workshops, online courses, and instructional videos to cater to different learning styles.
- Evaluation and Feedback: Implement assessments to gauge the effectiveness of the training and gather feedback for continuous improvement.
Maintenance Protocols Overview
- Maintenance protocols are critical for ensuring that systems operate smoothly and efficiently over time.
- They help in identifying potential issues before they escalate into significant problems, thereby reducing downtime and repair costs.
Key Elements of Maintenance Protocols
- Regular Inspections: Schedule routine checks to assess the condition of the system and identify any wear and tear.
- Preventive Maintenance: Implement a preventive maintenance schedule that includes tasks such as software updates, hardware checks, and system backups.
- Documentation: Maintain detailed records of maintenance activities, including dates, tasks performed, and any issues encountered.
- User Training on Maintenance: Train users on basic maintenance tasks they can perform, such as cleaning, software updates, and troubleshooting common issues.
Steps to Implement Training and Maintenance Protocols
- Step 1: Define Objectives: Establish clear goals for both training and maintenance protocols.
- Step 2: Develop a Schedule: Create a timeline for training sessions and maintenance checks.
- Step 3: Assign Responsibilities: Designate team members responsible for conducting training and maintenance activities.
- Step 4: Create Training Materials: Develop manuals, guides, and other resources to support training efforts.
- Step 5: Conduct Training Sessions: Organize training sessions and ensure participation from all relevant users.
- Step 6: Perform Maintenance Checks: Execute scheduled maintenance tasks and document findings.
- Step 7: Review and Adjust: Regularly review the effectiveness of training and maintenance protocols and make necessary adjustments based on feedback and performance metrics.
Benefits of Robust Training and Maintenance Protocols
- Increased Efficiency: Well-trained users can operate systems more efficiently, leading to higher productivity.
- Reduced Downtime: Regular maintenance helps prevent unexpected failures, ensuring systems remain operational.
- Cost Savings: Proactive maintenance can save organizations money by avoiding costly repairs and replacements.
- Enhanced User Satisfaction: Users who feel confident in their abilities are more likely to be satisfied with their work and the systems they use.
In conclusion, implementing comprehensive training and maintenance protocols is vital for the successful operation of any system. By focusing on user education and proactive maintenance, organizations can ensure optimal performance and longevity of their technology investments. At Rapid Innovation, we specialize in developing tailored training and maintenance solutions that align with your business goals, ensuring that your systems not only function effectively but also contribute to a greater return on investment.














.svg)